Have you ever heard about Open Source Intelligence? Wondering what are Open Source Intelligence Examples? And how it is working? OSINT is a cost-effective and readily available way of using intelligence for enterprise cybersecurity management, as well as other business use cases.
Open-source intelligence is sourced from all over the Internet, and even though it provides a vast amount of data to work with, this also creates an overwhelming volume that must be fact-checked thoroughly for optimal results.
Now let’s consider in more detail what open-source intelligence is, how it works, and most importantly best open-source intelligence examples.
What Is Open Source Intelligence?
Open-source intelligence is a kind of data-driven intelligence that searches the internet and other public sources for information related to one’s query or search. In most cases, OSINT is employed to gather intelligence on a specific individual or group of people, an organization, or any other public entity strategically.
OSINT evolved before the internet and was a type of military espionage involving finding relevant information about adversaries in newspapers, radio broadcasts, as well as other publicly available data. Although the majority of data sources employed in OSINT nowadays are online or somehow digitized, it is still possible for an analyst to collect physical information from the public and open channels.
Also Read: Does Open-Source Software Have A Future?
How Does Open Source Intelligence Work?
One of the easiest ways to start using open-source intelligence for individuals and organizations is through a search engine query. Frequently, posing the right question regarding what demographic information you need is a first step to locating relevant open-source data entries that may provide more detailed information.
In addition to internet-wide data searches through search engines, you can also narrow down and target your search on specific platforms or databases such as a particular social media platform. However, you may also benefit from analyzing open-source threat intelligence feeds as well as other sources that often update large volumes of data.
If your data collection and analysis goals include working with large-scale sources of information such as databases, data lakes or live feeds manual searches and research are inefficient. In order to quickly go through a large number of intelligence, you may want to consider purchasing an advanced web scraper or OSINT tool that can automate and speed up the data analysis process.
Top 10 Open Source Intelligence Examples or Tools
Here we have a list of some top 10 open source intelligence examples or tools that will tell you the importance of Open Source Intelligence. Also, you can simplify your work process by utilizing these tools in your businesses…
Maltego
Maltego is designed to reveal connections between people, companies, domains, and open information about individuals on the internet. It is also famous for the fact that it takes this sometimes astronomical amount of found information and plots everything out in easy-to-read charts and graphs. The charts do a good job of converting raw intelligence into actions, and each chart can have up to 10 thousand data points.
Maltego works by automating the search of various public data sources so that users can click on one button and perform several queries. A search plan is defined as a “transform action” by the program, and Maltego comes pre-loaded with several such actions that include popular sources of public information like DNS records, whois records, search engines, and social networks.
Mitaka
Mitaka can be used as a Chrome extension or Firefox add-on, and it allows you to search over sixty different search engines for IP addresses, domain URL hashes ASNs Bitcoin wallet address I. The extension also saves you time by being a shortcut link to multiple online databases that can be searched with one click. An alternative extension Sputnik is also available for those who prefer such a focused, limited set.
Shodan
Shodan is the search engine of hackers while Google is that for everyone. It will not display the result like other search engines but it will show in a way that is easily understandable by any security professional. One of the significant entities for a certified information security professional is digital assets and networks. Shodan gives you a lot of knowledge regarding the assets that have been hooked up to the network. Devices can range from computers, laptops, webcams, and traffic lights to various IOT devices. This can allow security analysts to identify the target and assess it for different vulnerabilities, default settings or passwords, available ports banners and services, etc.
Spiderfoot
Spiderfoot is a free OSINT recon tool that integrates with several data sources and collects IP addresses, CIDR ranges, domains and subdomains ASNs email addresses phone names usernames BTC addresses, etc. Available on GitHub it has both a command line interface and a web server embedded to provide an intuitive web-based GUI The application itself has over two hundred modules which is perfect for red teaming reconnaissance activities to find more information on a target or identify what you may be exposing unintentionally online.
Spyse
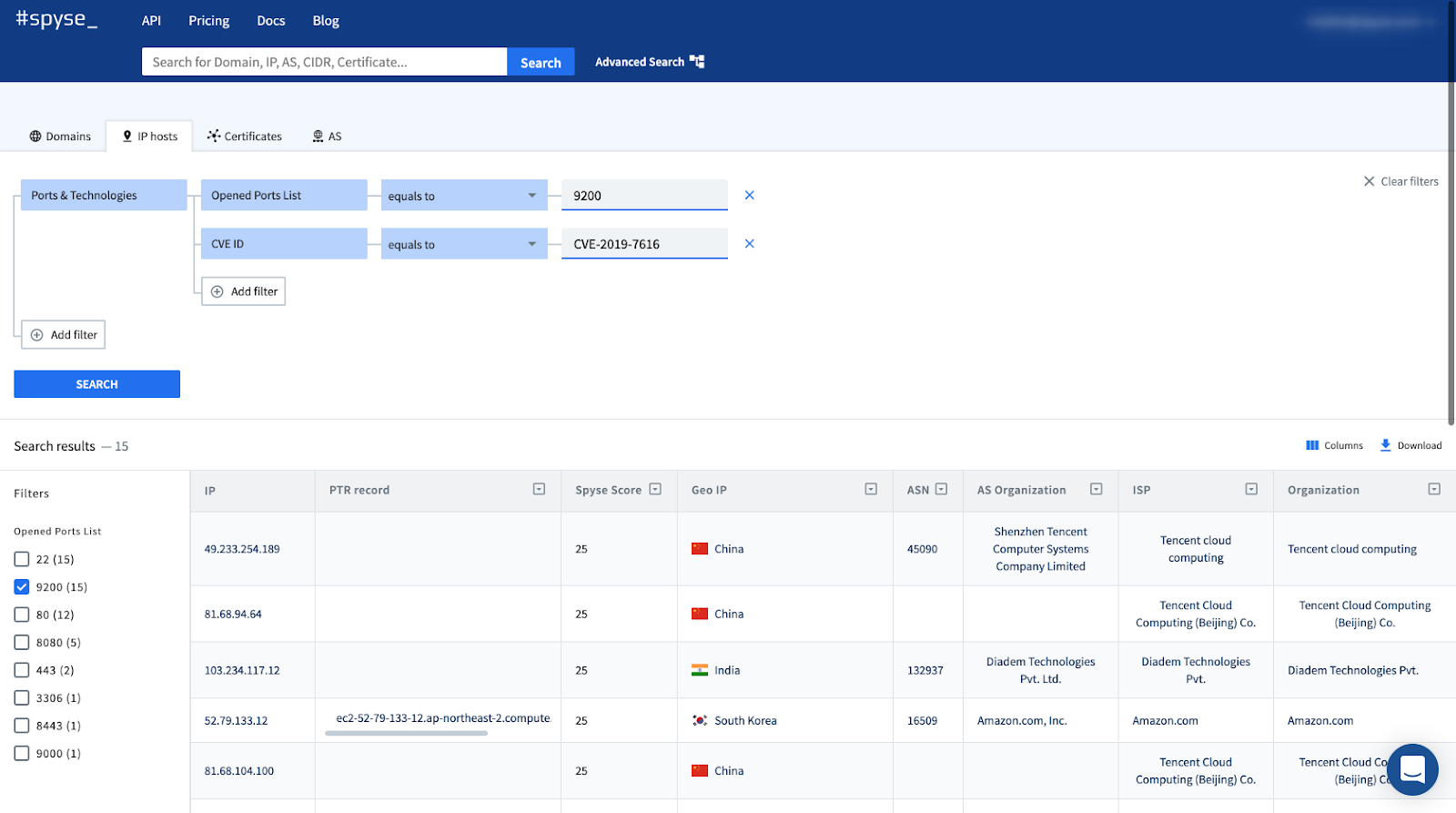
Spyse refers to itself as the “comprehensive internet assets registry for cybersecurity professionals.” Spyse, which is used by projects such as OWASP, IntelligenceX, and the previously mentioned Spiderfoot to collect publicly available information on websites their owners associated servers, and IoT devices. This information is then processed by the Spyse engine to identify any security threats in and between these various bodies. A free plan is offered, but developers hoping to build apps using the Sypse API may need paid subscriptions.
-37065cf143c4f94f.png)
Free OSINT tools such as Google, Bing, and DuckDuckGo are more than enough. If you are familiar with advanced filters. In brief, it is about fine-tuning your query to leverage the indexing capabilities of some of the world’s best algorithms. Talented researchers have learned over time to reverse-engineer search engines. This method is known as Google dorking or hacking and utilizes search operators (or functions) to increase the functionality of tools it works with other than Google too. The approach is debatable, as it may overstep the mark in terms of how public the information is.
Similar to this: Top 10 Open Source Technologies and Why You Should Learn Them
BuiltWith
As the name suggests, BuiltWith allows you to discover what popular sites are made of. There are different tech stacks and platforms that power various sites. For instance, BuiltWith can determine if a website is running on WordPress, Joomla, or Drupal as its CMS and provide more details. BuiltWith also produces a clean list of known JavaScript/CSS libraries that any given website uses (e.g., jQuery or Bootstrap). In addition, the service enumerates installed plugins on websites, frameworks, and other server information such as analytics and tracking data, etc BuiltWith is used for reconnaissance purposes.
Intelligence X
-89365cf143caaaf4.png)
Intelligence X is the first archival service and search engine that retains not only historic copies of web pages but also leaked datasets in their entirety which are usually removed from the Internet because of objectionable content or for legal reasons. While that may seem like what Wayback Machine of the Internet Archive does, Intelligence X has some significant differences in terms of content they concentrate on preserving. No matter how controversial the data sets may be, Intelligence X does not discriminate when it comes to preserving them.
DarkSearch.io
-73965cf143cb30e8.png)
Whereas experienced users of the dark web may already know where to search for what, DarkSearch.io can be a good starting point for newcomers in their research activities. Similar to Ahmia, the other dark web search engine DarkSearch is free and has a free API for automated searches. While Ahmia and DarkSearch have .onion sites, you do not need to go into the. onion versions or use Tor for accessing either of these search engines. Accessing darksearch.io from an ordinary internet browser will allow you to perform a deep web search.
Metagoofil
Metagoofil is another free tool that can be found on GitHub and it has been designed to extract metadata from publicly available documents. Metagoofil can analyze almost any document that it is able to obtain via public channels such as .pdf, doc.ppt, xls, and many others. Metagoofil gathers impressive amounts of interesting data. The searches yield items like the username for found documents, and real names if available. It also traces paths leading to those documents, which would include server names, shared resources, and directory tree information on the host organization.
Sum up
To sum it up, the Top 10 Open Source Intelligence examples show how we can gather useful information from public sources. Whether it's checking social media for opinions, looking at government records, or studying maps and images, OSINT covers a wide range of ways to learn and understand things. It's like using freely available information to get insights about different topics, but it's important to do it ethically and legally. Overall, these examples highlight the diverse and valuable ways OSINT can be applied in various areas of interest.
FAQs
One form of open-source information is public data or content that can be used by anyone without any restrictions. This may include data from sources such as government databases, public records, websites, and social media posts.
There is no best OSINT (Open Source Intelligence) tool because it all depends on specific needs. Popular ones are Maltego, Shodan, and OSINT Framework for a wide range of information gathering. It is recommended to apply a set of tools that are suitable for the context and purposes of investigation.
The actual percentage of open source intelligence is not known but a considerable amount, estimated to be somewhere between 80-90%, can always be said to have been derived from the sources public.
Yes, Google can be regarded as an OSINT (Open Source Intelligence) tool because it provides a means to access public data on the internet.

